Web programming (PORTABL EDEMA MONITORING SYSTEM
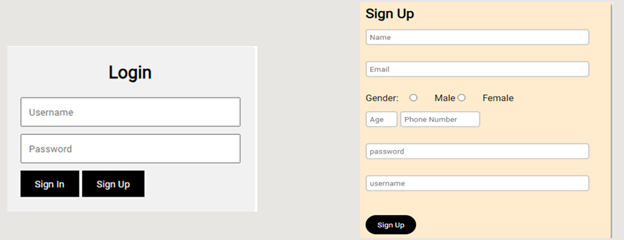
Connecting the outputs coming from the sensor and converting them into a highly efficient software system was one of the most important challenges that we were able to overcome with all capabilities. The software system includes two parts, one for the doctor responsible for the patient’s condition, which is the website, where we created pages for sign in and sign-up data only for the doctor, which provides a high percentage of confidentiality of patients’ information, such as name, email, and phone number, in addition to gender and age. The second part talks about the app, which is main responsible for receiving data on resistance changes edema from Bluetooth technology directly then sending this information for website to show for the doctor. The following figure clearly shows the life cycle of data from and to the website and application, passing through the database until it finally reaches the doctor and patient at the appropriate time
Security and performance are the main criteria that we took into consideration during the creation our system. For the website we placed a higher emphasis on security due to the presence of pages that have patient information. For the application performance was the most important factor because most of the people with edema are elderly people who usually cannot wait for security procedures also because their lower level of information sensitivity
First Trial
During this phase we have established just the basic rules and structure we need to build our software system. For example, on the website we have placed a login page and another page to register information. In the same way, in the application, we have a quick login page, in addition to another page for connecting to Bluetooth and displaying the required values.
Weaknesses
• Need more security.
Second Trial
In this part, we developed the security rate to become more powerful in the software system with the database, specifically regarding the security of passwords, so that we make it difficult for hackers to attack or exploiting any vulnerability for hack the website.
Password History One of the principles of security revolves around the idea of preventing any new username and password from entering the website if there is a similar one in the database. This technique makes it difficult for hackers to attempt to attack the website if there are any known previous passwords.
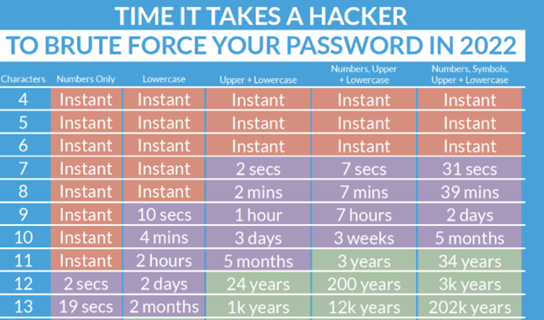
Password Complexity Another security principle that has been applied is password complexity. Password complexity ensures that specific controls and standards are set for the password, such as the number of fields and the presence of upper- and lower-case letters and symbols. Password complexity greatly protects against Brute force attacks common in the hacker world. In our case we limited the number of fields to 12 with uppercase and lowercase letters and symbols based on several points: A long time to break a password taking 3000 years in the event of a Brute force attack. Not long where is difficult for the user to memorize or short where easy to discover.
Preventing SQL injection attacks SQL Injection attacks mean exploiting a security vulnerability exist in the SQL query file. Usually, the hackers enter malicious or incorrect data or values with the aim of either obtaining sensitive information in the database or destroying the data and making it vulnerable. To prevent against these attacks, we have implemented SQL processing feature.